“Attributing Cyber Attacks,” with Ben Buchanan, Journal of Strategic Studies, 2015, February, vol 39, iss 1, p. 4-37, DOI:10.1080/01402390.2014.977382
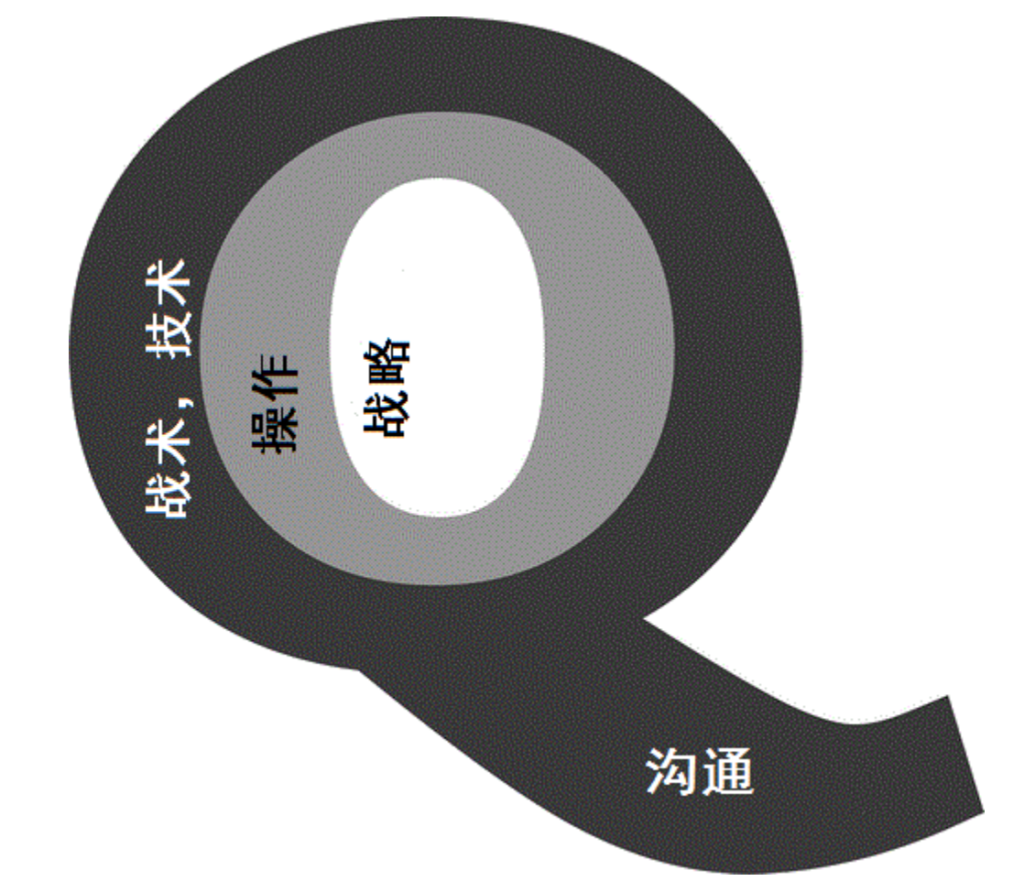 Who did it? Attribution is fundamental. Human lives and the security of the state may depend on ascribing agency to an agent. In the context of computer network intrusions, attribution is commonly seen as one of the most intractable technical problems, as either solvable or not solvable, and as dependent mainly on the available forensic evidence. But is it? Is this a productive understanding of attribution? — This article argues that attribution is what states make of it. To show how, we introduce the Q Model: designed to explain, guide, and improve the making of attribution.
Who did it? Attribution is fundamental. Human lives and the security of the state may depend on ascribing agency to an agent. In the context of computer network intrusions, attribution is commonly seen as one of the most intractable technical problems, as either solvable or not solvable, and as dependent mainly on the available forensic evidence. But is it? Is this a productive understanding of attribution? — This article argues that attribution is what states make of it. To show how, we introduce the Q Model: designed to explain, guide, and improve the making of attribution.
In Japanese: Thomas Rid and Ben Buchanan (translated by Motohiro Tsuchiya), “Cyber Kogeki wo Okonau no ha Dare ka (Attributing Cyber Attacks),” Senryaku Kenkyu (Journal of Strategic Studies), 18, 2016, 59-98. (Japanese PDF)
In Chinese: translated by a government-affiliated entity in Beijing (Chinese PDF).
On Google Scholar
On Altmetric
Coverage and mentions by Quartz, TIME, Heise, Telegraph, Bruce Schneier, Eugene Kaspersky, Richard Bejtlich (before the Permanent Select Committee on Intelligence in the US House of Representatives).
Launched at RUSI in London on 11 February 2015.
Briefed at the US Department of Defense, OSD, and a PLA workshop in Beijing, among others.